- Introduction
- What is CIA Triad in Cyber Security?
- Examples of CIA Triad
- Brief History of the CIA Triad
- Why Should You Use the CIA Triad?
- When Should You Use the CIA Triad?
- Importance of the CIA Triad
- Implementation of the CIA Triad
- Free Resources
Introduction
CIA Triad – What is the first thing that comes to mind when you think of the CIA triad? The US Secret Agency that hunts the dangerous criminals down? Well, this CIA triad is related to cyber security. Let us learn about CIA Triad in detail in this blog.
What is CIA Triad in Cyber Security?
CIA stands for Confidentiality, Integrity, and Availability.
CIA triad is a prominent model that serves as the foundation for the creation of security systems. They are used to identify weaknesses and develop strategies for problem-solving.
The CIA triad divides these three concepts into different focal points because they are essential to the running of a business: confidentiality, integrity, and availability of information. This distinction is useful because it directs security teams in determining the many approaches they might take to each issue. When all three requirements have been completed, the organization’s security profile should be stronger and more prepared to cope with threatening situations.

Let us now take a look at the three principles of the CIA triad in detail.
1. Confidentiality
The efforts made by an organisation to keep data private or hidden are referred to as confidentiality. To do this, access to information must be restricted to avoid the purposeful or unintentional sharing of data with unauthorised parties. Making sure that individuals without the appropriate authority are barred from accessing assets crucial to your firm is a crucial part of protecting confidentiality. On the other hand, a good system also makes sure that individuals who require access have the proper rights.
For instance, employees involved in managing an organization’s finances should have access to spreadsheets, bank accounts, and other data pertaining to cash flow. However, it’s possible that only a small number of CEOs and the great majority of other staff members will have access.
Confidentiality can be breached in a number of ways. This can entail making direct attacks on systems the attacker doesn’t have permission to access. Additionally, it can involve an attacker attempting to directly access a database or programme in order to steal or modify data.
These direct cyber attacks might employ strategies like man-in-the-middle (MITM) attacks, in which the attacker inserts themself into the information stream to intercept data and either take it or modify it. Other kinds of network eavesdropping are used by certain attackers to access credentials. To get the next level of clearance, the attacker may occasionally try to obtain further system privileges.
However, not all breaches of privacy are deliberate. It’s also possible that human error or inadequate security measures are at fault. Eg. Someone might fail to protect their password either personal or professional account. They might leave accounts logged in with no proper security or share it with someone else with the trust which leaves the account’s security vulnerable.
Use encryption methods to protect your data so that even if the attacker has access to it, they won’t be able to decrypt it. This is one of the main ways to avoid this. AES (Advanced Encryption Standard) and DES are examples of encryption standards (Data Encryption Standard). Through a VPN tunnel, you may also protect your data. Virtual Private Network, or VPN, enables secure data transmission over networks.
2. Integrity
Integrity requires ensuring that your data is reliable and unaltered. Only if the data is dependable, accurate, and legitimate will the integrity of your data be preserved.
We utilise a hash algorithm to determine whether or not our data has been altered.
We use the SHA (Secure Hash Algorithm) and MD5 types (Message Direct 5). Now, if we’re using SHA-1, MD5 is a 128-bit hash and SHA is a 160-bit hash. We could also utilise additional SHA techniques like SHA-0, SHA-2, and SHA-3.
Assume Host “A” desires to communicate data to Host “B” while retaining integrity. The data will be passed through a hash function to generate an arbitrary hash value H1, which is then appended to the data. The same hash function is applied to the data by Host “B” upon receipt of the packet, yielding the hash value “H2.” If H1 = H2, the data’s integrity has been upheld and the contents have not been altered.
3. Availability
This implies that users should have easy access to the network. This holds true for both systems and data. The network administrator must maintain gear, perform regular upgrades, have a fail-over strategy, and avoid network bottlenecks in order to guarantee availability. A network may become unusable due to attacks like DoS or DDoS as its resources are depleted. The companies and individuals who depend on the network as a commercial tool may feel the effects quite strongly. Therefore, appropriate steps should be made to stop such attacks.
Also, organizations can utilise redundant networks, servers, and applications to guarantee availability. These can be set up to become accessible if the main system is down or broken. Maintaining software and security system updates will help you increase availability. By doing this, you reduce the possibility that a programme may malfunction or that a recently discovered malware would penetrate your system. Backups and comprehensive disaster recovery strategies can also assist a business in quickly regaining availability following a bad incident.
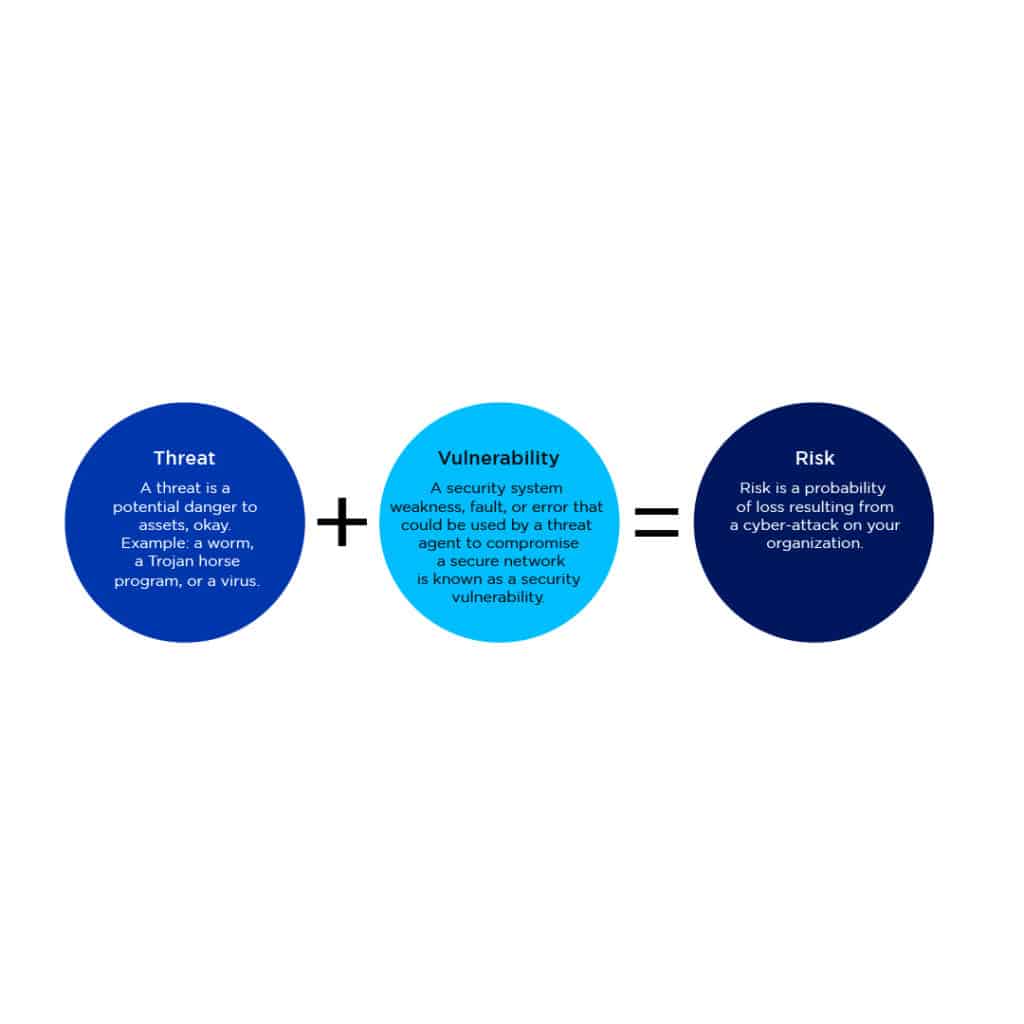
Examples of CIA Triad
Let us know how to try to understand how the CIA works with a real-life example. Think of an ATM where customers may check their bank balances and other information. An ATM has safeguards that address the triad’s basic ideas:
- Before granting access to sensitive data, two-factor authentication (a debit card with a PIN code) ensures confidentiality.
- By preserving all transfer and withdrawal records made via the ATM in the user’s bank accounting, the ATM and bank software ensure data integrity.
- The ATM offers accessibility because it is open to the public and available constantly.
Brief History of the CIA Triad
The CIA Triad evolved over time as information security specialists shared knowledge rather than having a single advocate. The 1976 U.S. Air Force study is where confidentiality was formally codified. On the other hand, integrity was discovered in a 1987 paper that indicated that business computers need particular attention to data accuracy. Although the exact origin of availability is unclear, it gained popularity in 1988 as a result of the Morris worm attack, which had disastrous consequences on thousands of important UNIX machines at the time and required partitioning the internet for days to clean up the mess. It is estimated that the fundamental idea of the CIA was established in 1988.
Why Should You Use the CIA Triad?
The CIA triad offers a straightforward yet thorough high-level checklist for assessing your security protocols and equipment. All three requirements—confidentiality, integrity, and availability—are met by an efficient system. A system of information security that falls short in one of the three CIA triangle components is insufficient.
The CIA security triangle is useful in determining what failed and what succeeded following a negative event. For instance, it’s possible that availability was impacted during a virus assault like ransomware, but the mechanisms in place were still able to protect the confidentiality of crucial data. This information can be used to strengthen weak areas and repeat effective strategies.
When Should You Use the CIA Triad?
The CIA triad should be used in the majority of security scenarios, especially since each element is crucial. However, it is especially useful when creating systems for classifying data and controlling access credentials. When dealing with your organization’s cyber vulnerabilities, you should strictly apply the CIA triad. It can be an effective tool for stopping the Cyber Kill Chain, which is the procedure for identifying and carrying out a cyberattack. You can use the CIA security triad to identify potential targets for attackers and then put policies and mechanisms in place to adequately defend those assets.
You can also use the CIA triad when training employees regarding implementing cybersecurity by using real-life use cases to make them understand easily.
Importance of the CIA Triad
Data theft and security breaches are causing organisations issues today. The unfavourable picture of the organization’s cybersecurity posture is reflected in the most recent reports and polls. The recent Facebook data breach controversy, in which the personal information of millions of users was leaked, is currently in the news. Due to lax standards, the majority of businesses have unsecured data, which might lead to data breaches and severe fines for failing to comply with regulations like the General Data Protection Regulation. The enterprises must implement the aforementioned security controls as well as other controls (like SIEM and SOAR) to strengthen their cybersecurity posture in order to avoid this predicament.
Implementation of the CIA Triad
An organisation should adhere to a general set of best practices when adopting the CIA triad. Following are some top techniques, broken down by each of the three topics:
1. Confidentiality
- Data should be handled in a proficient manner based on the organization’s rules of privacy.
- 2FA Encryption should be a must.
- Update file permissions, access control lists, and other settings on a regular basis.
2. Integrity
- To reduce human error, make sure staff members are aware of compliance and regulatory standards.
- Use software for backup and recovery.
- Use data logs, checksums, version control, access control, and security control to assure integrity.
3. Availability
- Use preventative measures like RAID, failover, and redundancy; and ensure the systems and applications are updated.
- Utilize server or network monitoring tools.
- In case of data loss, make sure a business continuity (BC) plan is in place.
Free Resources
- Cybersecurity for Leaders – An Introduction
- Cyber Security Executive Order
- Cyber Forensics
- Cyber Security For Leadership
FAQs
The CIA Triad is an information security model, which is popularly known to ensure data security for businesses and organisations. The full form of the CIA stands for its three principles – Confidentiality, Integrity, and Availability.
The CIA Triad can be used to more effectively decide which of the three principles will be most beneficial for a given collection of data as well as for the organisation as a whole and help in information security for organisations.
Examples: E-commerce sites generally use these CIA triad principles:
Confidentiality: A password is required to log in. You might be required to enter a code that has been emailed to you or engage in another type of two-factor authentication if it has been a while since your last log in.
Integrity: To ensure that your purchases are represented in your account and that you can contact a representative if there is a discrepancy, data integrity is offered.
Availability: You can access your account at any time, and you may even be able to get in touch with customer service day or night.
CIA stands for its three principles – Confidentiality, Integrity, and Availability.
A prominent model that serves as the foundation for the creation of security systems is the CIA triad. They are used to identify weaknesses and develop strategies for problem-solving.
The three fundamental components of an information security concept known as the CIA triad are confidentiality, integrity, and availability.








